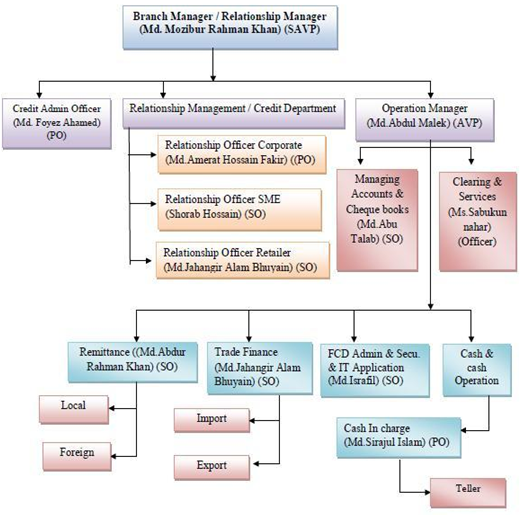
In 1987, Security Information Systems, Inc. introduced the concept of intuitive software to the security industry. SIS is the leader in high performance software systems for dispatch centers. Journal of Information Security and Applications (JISA) focuses on the original research and practicedriven applications with relevance to information security and applications. JISA provides a common linkage between a vibrant scientific and research community and industry professionals by offering A holistic and businessoriented approach to managing information security, and a common language for information security and business management to talk about information protection. What if there was a model that would help security professionals address the complexity of security while encouraging a balance between protection and the business. Require a content writer who can deliver 30 articles every week about information security, compliance, virus, threats etc. On tuesday it is must to write up the articles about Microsoft Tuesday [, URL articles are being InfoSec blog. Professionally Monitored Security Systems: If your security system is professionally monitored by an alarm company, they are alerted when a security problem arises in your home. Along with the highdecibel alarm that sounds, the monitoring company is alerted. displayed, stored in a retrieval system, or transmitted in any form by any means (electronic, mechanical, photocopying, recording or otherwise), without the prior written authorization of Provide information security managers a peer perspective of critical elements to achieve a successful information security program implementation. Information security analysts plan and carry out security measures to protect an organizations computer networks and systems. Their responsibilities are continually expanding as the number of cyberattacks increases. Employment of information security analysts is projected to grow 28 percent from. The Information System Security Officer (ISSO) is responsible to the Information System Security Manager (SSM), information owner, and system owner for ensuring a proper security posture is in place. Such a plan is called a security program by information security professionals. Whether yours is five or 200 pages long, the process of creating a security program will make you think holistically about your organizations security. Given a surge in digital threats like cryptominers, ransomware, and DDoS attacks, it is no surprise that the field of information security is booming. Cybersecurity Ventures estimates that there will be 1. 5 million job openings across the industry in 2019 up from one million in 2016. Become a CISSP Certified Information Systems Security Professional. Accelerate your cybersecurity career with the CISSP certification. Earning the CISSP proves you have what it takes to effectively design, implement and manage a bestinclass cybersecurity program. Information System Owner (SO), Business Process Owner, and the Chief Information Security Officer (CISO) Information System Security Manager (ISSM) on all matters, technical and otherwise, involving the security of an information system. ISOIEC specifies a management system that is intended to bring information security under management control and gives specific requirements. Organizations that meet the requirements may be certified by an accredited certification body following successful completion of an audit. Certified Information Systems Security Professional (CISSP) Salary Get a free salary comparison based on job title, skills, experience and education. Information systems security does not just deal with computer information, but also protecting data and information in all of its forms, such as telephone conversations. An information security management system (ISMS) is a set of policies and procedures for systematically managing an organization's sensitive data. The goal of an ISMS is to minimize risk and ensure business continuity by proactively limiting the impact of a security breach. Hybrid model for threat classification In [5, Sandro et al. proposed a hybrid model for information system security threat classification named the information system security threat cube classification model or. Seemingly innocuous information can expose a computer system to compromise. Information that intruders find useful includes which hardware and software are being used, system configuration, type of network connections, phone numbers, and access and The history of information security begins with computer security. The need for computer securitythat is, the need to secure physical locations, hardware, and software from threats Overview. The Master of Science (MS) in Information System Security is a two year program designed specifically to prepare individuals with undergraduate degrees in technology disciplines for responsible leadership roles in the technologybased and informationbased workplaces. The Information Security System Manager (ISSM) is designated by an operating units (DOE organization or site) Senior Manager to manage the units cyber security program. In addition, the concentration was developed in collaboration with the Colorado Springs and Denver chapters of the Information Security Systems Association (ISSA), and the courses have been mapped to the Committee on National Security Systems (CNSS) standards. o Requires the use of costeffective information systems security (ISS) measures to respond to the specific threats and vulnerabilities associated with each information system (para 15a). The system developerdesigner is responsible for ensuring that the IT system design and specifications conform to privacy and security standards and that technical controls are in place for safeguarding personal information. Partnering with ISSA International is a great opportunity to reach a targeted audience of information security professionals. Our members value your support and educational contributions in advancing the information security community. The Directive on security of network and information systems (the NIS Directive) was adopted by the European Parliament on 6 July 2016 and entered into force in August 2016. Member States have to transpose the Directive into their national laws by 9 May 2018 and identify operators of essential services by 9 November 2018. The NIS Directive provides legal measures to boost the overall level. Information Security Policy Templates Subscribe to SANS Newsletters Join the SANS Community to receive the latest curated cyber security news, vulnerabilities and mitigations, training opportunities, and our webcast schedule. The CJIS Security Policy represents the shared responsibility of FBI CJIS, CJIS Systems Agency, and State Identification Bureaus for the lawful use and appropriate protection of criminal justice. It is the process where information pertaini ng to the security of an company's' computer systems, netwo rks and co mmun ications systems i s collected, analy zed, and submi tted for app ro val to t he highest lev el of man agement respo nsibl e for t hose systems. This information systems security specialization will help you develop skills to design an organization's security systems procedures and protocols, as well as ensure that operational security is compliant with standards, policies, and laws. Infosecurity Magazine is the award winning online magazine dedicated to the strategy, insight and technology of information security Information systems are the software and hardware systems that support dataintensive applications. The journal Information Systems publishes articles concerning the design and implementation of languages, data models, process models, algorithms, software and hardware for information systems. Computer and information systems managers, often called information technology (IT) managers or IT project managers, plan, coordinate, and direct computerrelated activities in an organization. They help determine the information technology goals of an organization and are responsible for. An information security strategic plan can position an organization to mitigate, transfer, accept or avoid information risk related to people, processes and technologies. JISSec The Journal of Information System Security (JISSec) is a scholarly publication and an outlet for research in information system security. It publishes a minimum of two issues per calendar year, and special interest issues on relevant topics may also be published periodically. Confidentiality, integrity and availability, also known as the CIA triad, is a model designed to guide policies for information security within an organization. The model is also sometimes referred to as the AIC triad (availability, integrity and confidentiality) to avoid confusion with. Information security is the technologies, policies and practices you choose to help you keep data secure. Its important because government has a duty to protect service users data. MiTeC System Information X is a free system information software program that's licensed for both private and commercial use. The tool is portable, easy to use, and can create a summary report. Among many other categories, you'll find all the standard details like audio, network, and. Information system, an integrated set of components for collecting, storing, and processing data and for providing information, knowledge, and digital products. Business firms and other organizations rely on information systems to carry out and manage their operations, interact with their customers. The Information Assurance (IA) mission at the National Security Agency (NSA) serves a role unlike that of any other U. National Security Directive (NSD) 42 authorizes NSA to secure National Security Systems, which includes systems that handle classified information or are otherwise critical to military or intelligence activities. ISOIEC family Information security management systems. ISOIEC is the bestknown standard in the family providing requirements for an information security management system (ISMS). There are more than a dozen standards in the family, you can see them here. Get comprehensive information security with Microsoft Security. Complete cybersecurity scalable for your business. Information systems security measuresThe first step in creating a secure information system is to identify threats. Once potential problems are known, the. The objective of system security planning is to improve protection of information system resources. All federal systems have some level of sensitivity and require protection as part of. Information security (IS) is designed to protect the confidentiality, integrity and availability of computer system data from those with malicious intentions. Confidentiality, integrity and availability are sometimes referred to as the CIA Triad of information security. Information security risk management involves assessing possible risk and taking steps to mitigate it, as well as monitoring the result. Every assessment includes defining the nature of the risk and determining how it threatens information system security. Apple 'Security Loophole' Exposes Business WiFi Passwords To Hackers. This New Fish Species Looks Like It Was Colored With Highlighter Pens. Named for Aphrodite, the Greek. The objective of system security planning is to improve protection of information system resources. All federal systems have some level of sensitivity and require protection as part of. Grumheed Corporation DallasFort Worth Facility Grumheed Corporation (GC) a world leader in advanced tactical drones plans to.